Just recently, cybersecurity experts unveiled a huge data breach. It involved an unbelievable 16 billion login credentials. These stolen records include usernames and passwords. They belong to users across nearly every major online service. Indeed, your social media, your email, and even your government portal logins could be out there for bad actors to see.
This huge leak did not come from just one attack. It is, in fact, a collection from many “infostealer” malware attacks. These sneaky software applications quietly gather your sensitive information from infected devices. You may not even know it is happening. Other recent incidents also wave red flags. Ransomware attacks, for instance, have severely crippled healthcare giants like Ascension. These attacks hold systems hostage until a payment is made. Data breaches have also affected big firms like LexisNexis Risk Solutions, exposing personal data of millions. The message is simple and clear: hackers are always busy, relentlessly looking for loopholes and vulnerabilities to exploit.
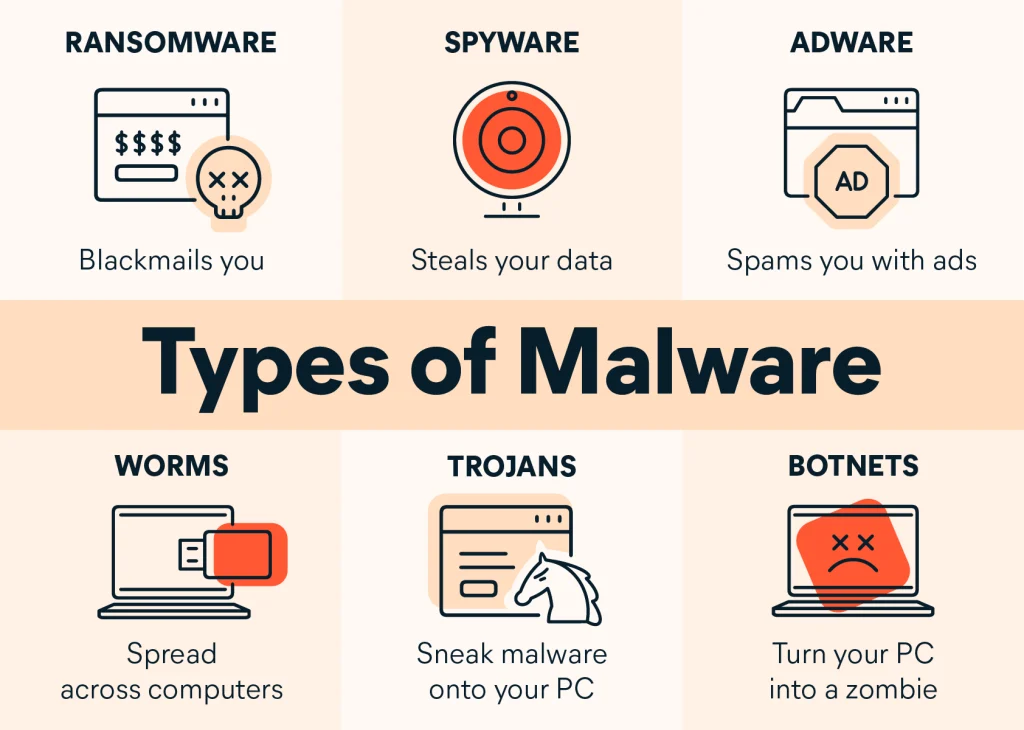
How These Cyber-Crooks Operate: Understanding Their Game
Hackers employ many sophisticated tricks. Understanding their game is your first line of defence.
Common Hacking Techniques
Phishing: This method is very common and dangerous. You typically receive fake emails or messages. They pretend to come from a trustworthy company, your bank, a government agency, or even someone you know. These messages trick you into clicking a dangerous link or opening a harmful attachment. They might create urgency. For example, they claim your account is locked. Or perhaps your payment has failed. Sometimes, they offer something too good to be true. All these tactics push you into quick action without thinking. Once you click that link, it can lead you to a fake website. This site looks exactly like the real one. It waits to steal your login credentials.
Malware: This is a broad term for malicious software. It includes nasty things like viruses, worms, and Trojans. Malware can creep onto your device through infected downloads, malicious websites, or even email attachments. Once inside, it can steal your valuable data. It can spy on your activities. Furthermore, it can even hijack your entire computer, taking control from you. Ransomware, a specific type of malware, locks your files. It then demands money for their release.
Keyloggers: These are specific tools, often a type of malware. They record every single key you press on your keyboard. This helps them capture incredibly sensitive information. This includes your passwords, banking details, and credit card numbers. You might not even realise it is happening. They essentially log everything you type.
Public Wi-Fi Traps: Free Wi-Fi in public spots like coffee shops, airports, or hotels can be very risky. Hackers can set up fake Wi-Fi hotspots that look legitimate. When you connect, they easily spy on your connection. They intercept your data. Subsequently, they steal your information as you browse or conduct online transactions. Always be very careful when using unsecured public networks.
Brute Force Attacks: This is a simpler, yet effective, method. Hackers use automated programs. These programs try millions of password combinations until they guess the correct one. Therefore, the longer and more complex your password is, the harder it is for them to succeed with this method.
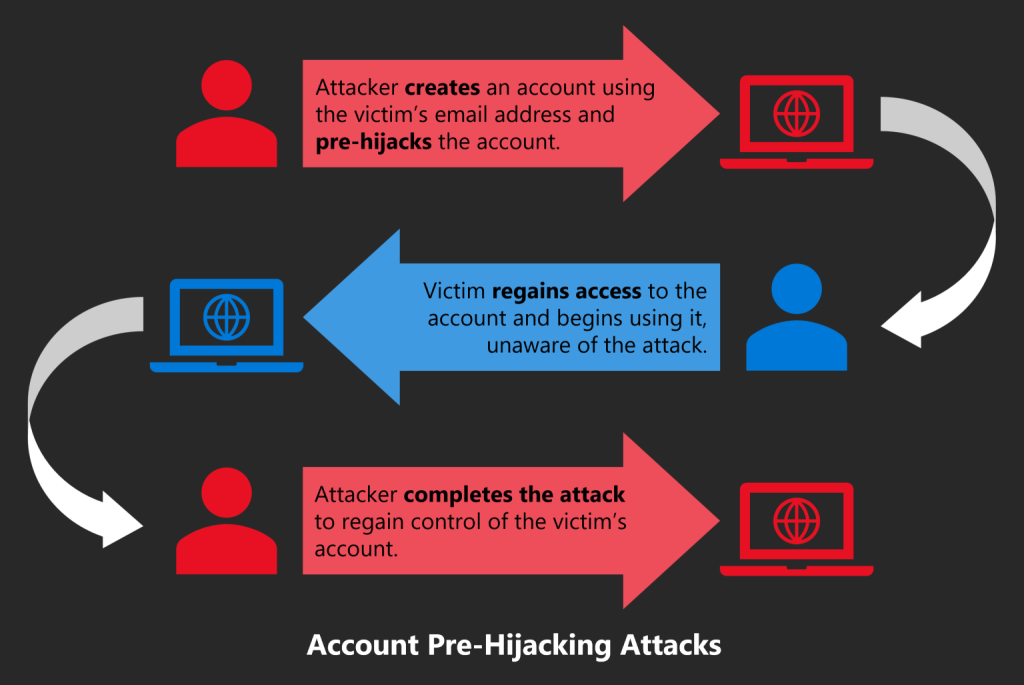
What Happens When Your Account Is Exposed? The Ripple Effect
When hackers successfully get hold of your digital details, many serious problems can follow. These issues impact not just you but potentially those around you. Your hard-earned money can disappear from your bank accounts or online wallets. This often leads to significant financial losses. Identity theft is a huge risk. Criminals use your stolen personal information – like your name, address, or even Social Security number – to open new accounts. They apply for loans. They commit other fraudulent activities in your name. This causes massive headaches and long-term financial distress.
Your personal information, including private photos, confidential documents, or sensitive conversations, might be exposed. This data can appear on the dark web or public forums. Even worse, hackers might use your compromised accounts to trick your friends, family, or business contacts. They send them malicious links or request money. This can create a chain of trouble for many people connected to you.

Your Digital Shield: Protecting Your Accounts Like Gold
Guarding yourself is not as hard as it sounds. However, it requires consistent effort. Simple, deliberate steps can make a very big difference in protecting your online life.
Essential Security Measures
Strong, Unique Passwords: This is your first and most fundamental defence. You must use a different, complicated password for every single online account. Make them truly long, ideally at least 12 to 16 characters. Mix uppercase and lowercase letters. Add numbers and include special symbols (like !, @, #, $, %). Furthermore, avoid using common words, easily guessable sequences, or any personal details like your birth date, pet’s name, or family member’s name. Consider using a reputable password manager. These tools help you create incredibly strong, unique passwords for all your accounts. They store them securely in an encrypted vault. This removes the burden of remembering dozens of complex combinations.
Two-Factor Authentication (2FA): Switch this on for all your important accounts without fail. This adds an extra, critical layer of security. Think of it like an extra padlock on your digital door. Even if hackers manage to guess or steal your password, they still cannot log in without this second verification step. This might be a unique code sent to your mobile phone via SMS. Or it could be a code generated by an authenticator app (like Google Authenticator or Authy). Sometimes, it is even a quick fingerprint scan. Always choose the authenticator app or security key option over SMS when available. This is because SMS codes can sometimes be intercepted.
Be Smart with Emails and Links: Always scrutinize the sender of any email or message. This is especially true if it seems unexpected or urgent. Look out for strange spellings, grammatical errors, or urgent, demanding requests. These often try to rush you into action. Never click on suspicious links, even if they look legitimate. And never open unexpected attachments. If you have even a tiny doubt about the message’s authenticity, do not engage. Instead, go directly to the company’s official website by typing the address into your browser yourself. Then, log in there to check for any alerts or notifications. Never use the link provided in the suspicious email.
Keep Software Updated: Make it a habit to always update the software on your mobile phone, computer, and all your applications. Do this as soon as updates are available. These updates often include critical security patches. Such patches fix vulnerabilities and close security holes that hackers might exploit. Turning on automatic updates for your operating system and apps ensures you always have the latest protections. This requires minimal effort from your side.
Avoid Public Wi-Fi for Sensitive Tasks: Never conduct online banking, sensitive shopping, or access private information while connected to public Wi-Fi networks. These connections are typically unsecured. They can be easily monitored by cybercriminals. Instead, use your mobile data connection, which is generally more secure. Alternatively, if you must use public Wi-Fi, invest in and use a Virtual Private Network (VPN). A VPN encrypts your connection. This creates a secure tunnel for your data. Thus, it makes it much harder for hackers to spy on your activities.
Monitor Your Accounts: Develop a routine of regularly checking your bank statements, credit card activity, and all your online accounts. Look for any strange transactions, unfamiliar logins, or unusual activity. Review activity logs on your social media platforms and email. If you spot anything out of the ordinary, report it to the relevant company, bank, or service provider immediately. Early detection can prevent much larger problems.
Be Careful What You Share Online: Exercise caution and discretion about the personal information you post on social media and other public platforms. Avoid putting up sensitive details. This includes your exact home address, precise travel plans, or even your daily routines. Set your social media profiles to private. This restricts who can see your posts and personal information. Only accept friend or connection requests from people you truly know and trust in real life. Remember, anything you post online can potentially be seen and used by others.
Stay Vigilant, Stay Safe: Your Digital Future in Your Hands
Cybersecurity is a responsibility for everyone, not just the tech gurus or IT professionals. By consistently following these simple, yet powerful, steps, you can significantly reduce your risk of becoming a victim of online fraud or hacking. Stay informed about new scams and cyber threats. Be cautious in all your online interactions. Protecting your digital life is just as important as protecting your physical assets. Your peace of mind, and the security of your finances and personal identity, truly depends on it.
You May Also Like: Insurers Say Cybersecurity Guidelines Will Prepare Sector for Protection and Opportunity
